P
In the next article we are going to take a look at Firejail. It may happen that on some occasions you are interested, for one reason or another, test more or less stable applications. In such cases, it is normal to worry about the security of your system. Something that in Gnu / Linux can be done, is to use these applications in a sandbox.
To be clear, it must be said that 'sandboxing'is the ability to execute applications in a sandbox. This provides the application with a fair amount of resources needed to run. Thanks to the application called Firejail, we will be able to safely run applications that are not trusted in Gnu / Linux. Firejail is a tool designed for security-conscious users, who seek to protect their system.
Firejail is a SUID program that reduces the risk of security breaches by restricting the runtime environment untrusted applications that use namespaces and seccomp-bpf. Allows a process and all its descendants to have their own private view of globally shared kernel resources such as the network stack, process table, mount table, etc.
This program has been written in C y practically no dependencies needed. The software runs on any Gnu / Linux machine with kernel version 3.x or newer. The sandbox is light, the overhead is low. There are no complicated configuration files to edit, no open socket connections, and no daemons running in the background. All security functions are implemented directly in the kernel. The program is released under the GPL v2 license.
Firejail can perform any type of process: servers, graphical applications and even user login sessions. The software includes security profiles for a large number of programs Gnu / Linux: Mozilla Firefox, Chromium, VLC, Streaming, etc.
General characteristics of Firejail
- Linux namespaces.
- File system container.
- Security filters.
- Network compatibility.
- Security profiles.
- Resource allocation.
- Graphical user interface.
Can be found detailed information about Firejail features in the official project page.
Install Firejail on Ubuntu
Installation can be done downloading the latest package from the project's Github page using git command in terminal (Ctrl + Alt + T):
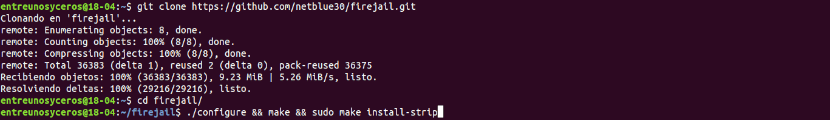
git clone https://github.com/netblue30/firejail.git cd firejail ./configure && make && sudo make install-strip
In case you don't have git installed on your system, you can install it with the command:
sudo apt install git
We will also be able to install Firejail by downloading the .deb package and using the package manager. This file can be downloaded from the SourceForge of the project.
Once you have downloaded the file, you can install the program by typing in a terminal (Ctrl + Alt + T):
sudo dpkg -i firejail_*.deb
How to run applications with Firejail on Gnu / Linux
Once the installation is finished, you are now ready to run the applications with Firejail. This is achieved by opening a terminal (Ctrl + Alt + T) and writing firejail before the command we want to execute.
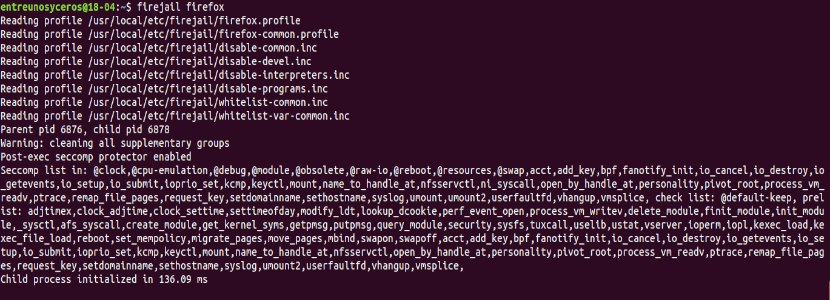
firejail firefox #Inicia el navegador web Firefox
Create security profile
Firejail includes many security profiles for different applications. If you have created the project from the source, you can find the profiles at:
ruta-a-firejail/etc/
If you have used the deb package, you can find the security profiles in:
/etc/firejail/
Users must place the profiles to be used in the following directory:
~/.config/firejail
If what you want is restrict application access to a certain directory, you can use a blacklist rule to accomplish exactly that. For example, the following can be added to your security profile to restrict access to the Documents folder:
blacklist ${HOME}/Documentos
Another way to achieve the same result is to write the full path to the folder that we want to restrict:
blacklist /home/user/Documentos
Security profiles can be configured in many different ways. You can disable access, allow read-only access, etc. If you are interested in create custom profiles, Can refer to the following FireJail instructions.