Nobody escapes that you have to look for improve security of our equipment as far as possible, this for both desktop computers and laptops, although in the case of the latter it is directly something imperative -especially if we use them for work- since the fact of taking them from one to the other another place increases the chances of losing it or having it stolen from us, and in both cases our information can be exposed and the consequences of this would be very serious.
The alternatives in this sense are a few, and that is the good thing about FOSS in general, although in this case I want to talk about DM-Crypt LUKS, an encryption solution very popular for a long time thanks to the fact that it is integrated into the kernel as a module - offering access to the Crypto APIs of the linux kernel- and offer Transparent encryption and the ability to map devices and partitions in virtual block levels, thus allowing encrypt partitions, entire hard drives, RAID volumes, logical volumes, files or removable drives.
To start we need have a free partition (in my case, / dev / sda4), so if that is not the case we will have to create a new partition using a tool like GParted. Once we have free space we are going to start with install cryptsetup if we no longer have this tool, which in general is usually included by default but perhaps when we install our Ubuntu we opted for a minimal installation:
# apt-get install cryptsetup
Now let's start with initialize partition what are we going to encrypt, for which we use that free partition that we mentioned earlier. This is a step that also generates the initial key, and although its name seems to indicate that the partition is formatted that does not happen, but simply prepares it to work with encryption (in our case we have opted for AES with a key size of 512 bytes:
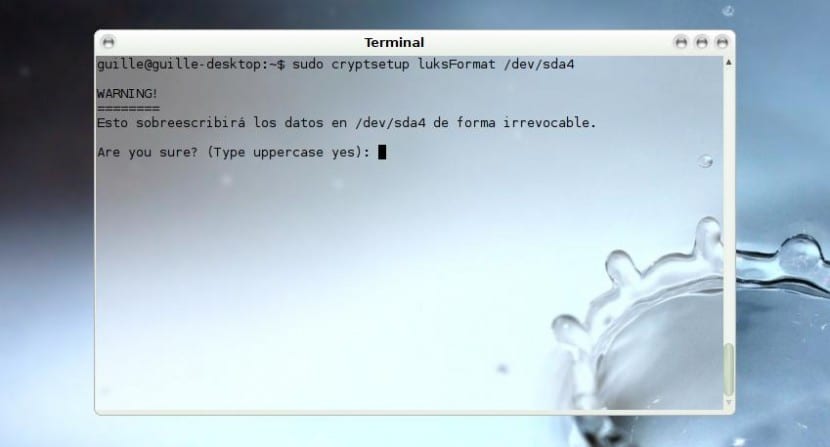
# cryptsetup –verbose –verbose –cipher aes-xts-plain64 –key-size 512 –hash sha512 –iter-time 5000 –use-random luksFormat / dev / sda4
We will receive a warning message where we are notified that the content that we have stored at this time in / Dev / sda4, and we are asked if we are sure. We agree by writing YES, like this in capital letters, and then we are asked to enter the phrase LUKS, twice to make sure there are no errors.
Now we 'open' the encrypted container, at the same time we give it a virtual name, which will be the one that appears in the system (for example when we execute the command df -h to visualize the different partitions, in our case we will see it in / dev / mapper / encrypted):
# crytpsetup luksOpen / dev / sda4 encrypted
We are asked to LUKS key that we have created previously, we enter it and we are ready. Now we must create the file system for this encrypted partition:
# mkfs.ext3 / dev / mapper / encrypted
The next step is to add this partition to the / etc / crypttab file, similar to / etc / fstab since it is responsible for providing the encrypted drives at system startup:
# cryto_test / dev / sda4 none luks
Then we create the mount point of this encrypted partition and add all that information to the / etc / fstab file so that we have everything available with each reboot:
# mkdir / mnt / encrypted
# nano / etc / fstab
Adding the following should be fine, although those looking for the most personalized can take a look at the fstab man pages (man fstab) where there is a lot of information about it:
/ dev / mapper / encrypted / mnt / encrypted ext3 defaults 0 2
Now, every time we restart the system we will be asked to enter the passphrase, and after doing so the encrypted partition will be unlocked so that we can have it available.
Thanks for your article.
I have a problem, I don't know if it happens to more people like me:
I follow the steps that you have detailed and after verifying that it is installed I start the second case–>
cryptsetup –verbose –verbose –cipher aes-xts-plain64 –key-size 512 –hash sha512 –iter-time 5000 –use-random luksFormat / dev / sda4
cryptsetup: Unknown action
I am using Kubuntu 15.04. Any idea how it can be solved.
Thank you