Firefox developers have released through an advertisement the inclusion of the mode Default DNS over HTTPS (DoH) for users in the United States. As of today, DoH it is enabled by default on all new installations by US users. whereas for current US users they are scheduled to switch to DoH in a few weeks. In the European Union and other countries, they still do not plan to activate DoH by default.
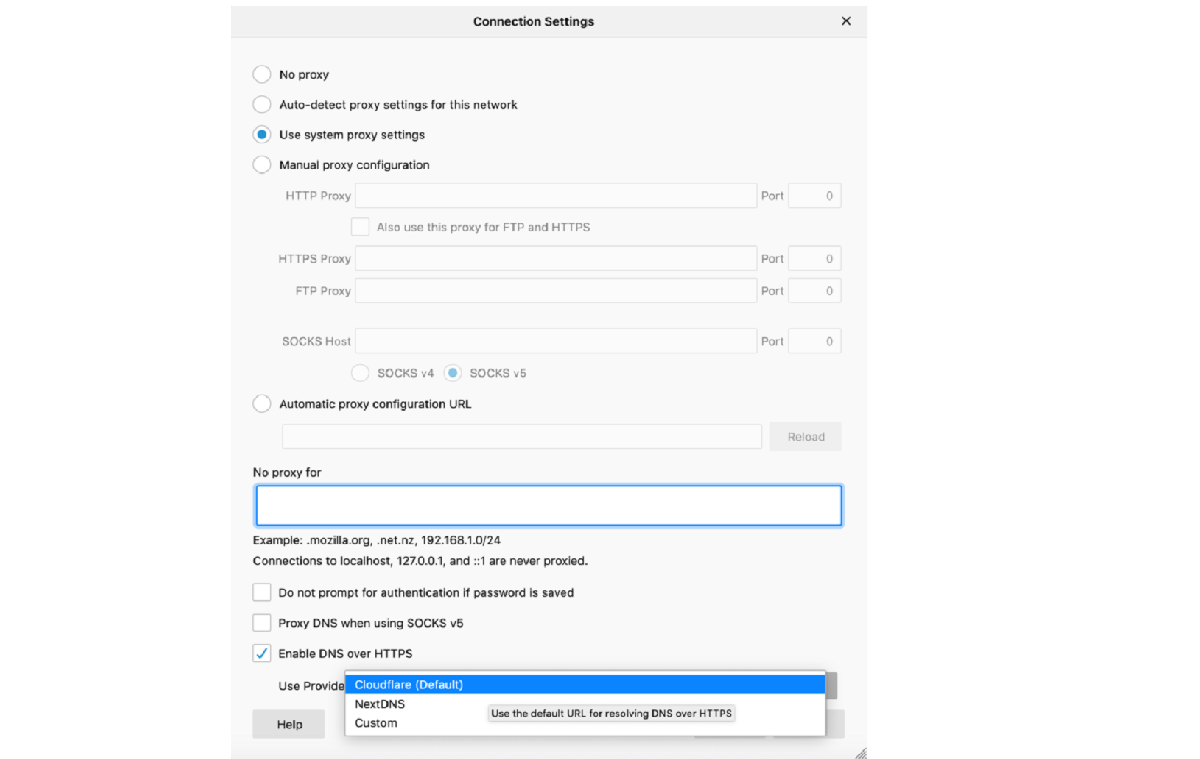
Users have the option to choose between two providers: Cloudflare and NextDNS, which are trusted solvers. After they activate DoH, they will receive a warning that allows the user to opt out of accessing the centralized DoH DNS servers and revert to the traditional scheme to send unencrypted requests to the provider's DNS server.
Instead of a distributed infrastructure of DNS resolvers, DoH uses a link to a specific DoH service, which can be considered as a single point of failure. The job is currently offered through two DNS providers: CloudFlare (default) and NextDNS.
Encrypting DNS data with DoH is just the first step. For Mozilla, requiring companies that handle this data to have established rules, such as those described in the TRR program, ensures that access to this data is not abused. Therefore, it is a must.
"For most users, it is very difficult to know where their DNS requests are going and what the resolver is doing with them," said Eric Rescorla, CTO of Firefox. "The Firefox Trusted Recursive Resolver program enables Mozilla to negotiate with vendors on its behalf and require them to have strict privacy policies before handling your DNS data." We are delighted that NextDNS is partnering with us as we work for people to regain control of their data and privacy online. "
The publisher is convinced that by combining the right technology (DoH in this case) and strict operational requirements for those who implement it, find good partners and establish legal agreements that prioritize privacy, by default it will improve user privacy.
It is important to remember that DoH can be useful to eliminate information leaks on the host names requested through the DNS servers of the providers, combat MITM attacks and replace DNS traffic (for example, when connecting to public Wi-Fi) and opposing DNS (DoH) blocking can not replace a VPN in the area of avoiding implemented blocks at the DPI level) or to organize work if it is impossible to directly access DNS servers (for example, when working through a proxy).
If in normal situations, DNS queries are sent directly to the DNS servers defined in the system configuration, then in the case of DoH, the request to determine the host's IP address is encapsulated in the HTTPS traffic and sent to the server HTTP in which the resolver processes requests through the web API. The existing DNSSEC standard uses encryption only for client and server authentication.
The use of DoH can cause problems in areas such as parental control systems, access to internal namespaces in corporate systems, path selection in content delivery optimization systems and compliance with court orders to combat the spread of illegal content and the exploitation of minors.
To get around such problems, a verification system has been implemented and tested that automatically disables DoH under certain conditions.
To make the change or deactivation of the DoH provider can be in the configuration of the network connection. For example, you can specify an alternate DoH server to access Google servers, in about: config.
The value of 0 completely disables, while 1 is used to enable whichever is faster, 2 uses the default values and with backup DNS, 3 only uses DoH and 4 is to use a mirror mode in which DoH and DNS are used in parallel.