IBM unveiled through an announcement opening the FHE toolkit (IBM Fully Homomorphic Encryption) with the implementation of a homomorphic encryption system complete to process data in encrypted form.
FHE It is characterized by allowing the creation of services for confidential computing in which encrypted data is processed and does not appear in open form at any stage. FHE supports full homomorphic operations that allow you to add and multiply encrypted data (that is, you can implement any arbitrary calculation) and get an encrypted result in the output, which would be similar to encrypting the result of adding or multiplying the original data.
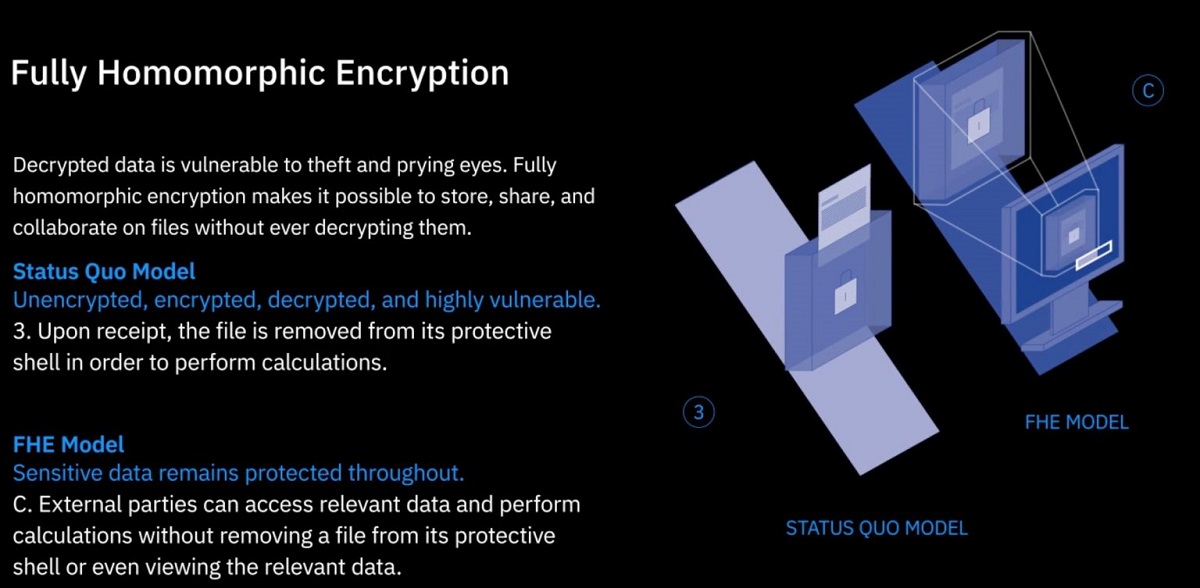
The FHE encryption can be considered as the next stage in the development of end-to-end encryption, In addition to protecting data transmission, data can be processed without decryption.
For IBM Z customers today, data can already be encrypted at rest and in flight with pervasive encryption. Customers can also protect data with data privacy passports on IBM Z, a consolidated data-centric protection and auditing (DCAP) technology * for eligible data that has the ability to protect data throughout its journey through of your company by establishing appropriate data protection controls.
However, we have never been able to keep data protected and processed simultaneously, a concept known as FHE.
About
The project has been developing since 2009, but only now has it been possible to achieve acceptable performance indicators that allow its use in practice.
It is observed that FHE makes available to all homomorphic calculationsWith the help of FHE, ordinary corporate programmers will be able to do the same job in a minute that previously required hours and days with the participation of experts with a scientific degree.
Among other developments in the field of confidential computing, you can see the publication of the OpenDP project with the implementation of differential privacy methods, which allow to perform statistical operations on a data set with sufficiently high precision without the possibility of identifying individual records in it.
The project is being jointly developed by researchers from Microsoft and Harvard University. The implementation is written in Rust and Python and is licensed under the MIT license.
Use cases
From a practical point of view, the framework can be useful for organizing cloud computing confidential, andn electronic voting systems, in anonymous routing protocols, for encrypted request processing in a DBMS, for confidential training of machine learning systems.
Experienced Docker developers can easily port this toolkit to their preferred distribution. The journey to mainstream FHE begins with these baseline implementations, but we anticipate that it will evolve with community involvement.
Today's announcement takes our commitment to Linux and security one step further to add in-use data security capabilities.
As an example of use by FHE, the organization of the analysis of information on patients from medical institutions is mentioned at insurance companies without the insurance company gaining access to information that can identify specific patients.
He also mentions the development of machine learning systems to detect fraudulent credit card transactions based on the processing of encrypted anonymous financial transactions.
The Toolkit includes HElib library with implementation of various encryption schemes homomorphic, an integrated development environment (I work through a browser) and a set of examples.
To simplify implementation, docked images have been prepareds ready to use based on CentOS, Fedora and Ubuntu. Instructions for building the toolkit from source and installing it on a local system are also available.
Finally, if you are interested in knowing more about it, you can check the details in the IBM announcement In the following link.