Pwn2Own 2033 was held in Vancouver
Recently the results of the three days of the competition Pwn2Own 2023, which is held annually as part of the CanSecWest conference in Vancouver.
In this new edition techniques have been demonstrated to work to exploit vulnerabilities previously unknown for Ubuntu, Apple macOS, Oracle VirtualBox, VMWare Workstation, Microsoft Windows 11, Microsoft Teams, Microsoft SharePoint and for Tesla vehicles.
A total of 27 successful attacks were demonstrated that exploited previously unknown vulnerabilities.
For those unfamiliar with Pwn2Own, you should know that this is a global hacking event organized by the Trend Micro Zero-Day Initiative (ZDI), which has been taking place since 2005. In it, some of the best hacking teams compete against technological targets. defaults and each other, using 'zero-day' exploits.
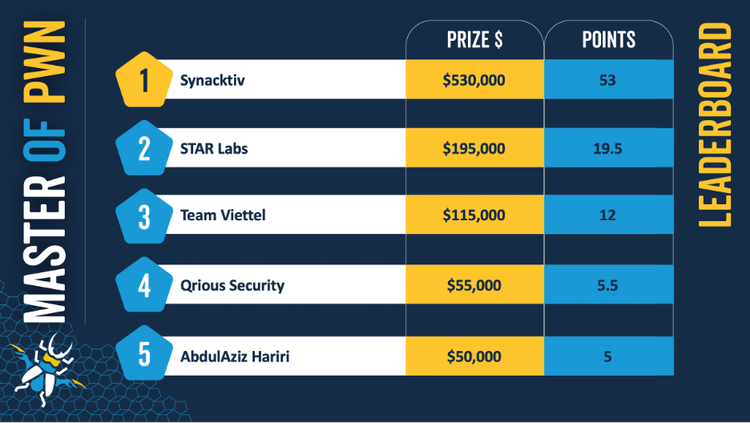
These elite hacker bounty hunters and security researchers have a strict time limit to successfully 'pwn' the targets in question. Success is rewarded both with points being added to a Masters of Pwn leaderboard, and kudos to Pwn2Own shouldn't be underestimated as the competitive nature is strong here, as well as impressive payouts. In total, Pwn2Own Vancouver 2023 has a prize fund of over $1 million.
The first to fall was Adobe Reader in the business applications category after Abdul Aziz Hariri (@abdhariri) from Haboob SA used a chain of exploits targeting a 6-bug logic chain that abused multiple failed patches that escaped the Sandbox and bypassed a list of banned APIs in macOS to win $50.000.
In the competition demonstrated five successful attempts to explode previously unknown vulnerabilities in Ubuntu Desktop, made by different teams of participants.
The problems were caused by the double freeing of memory (a $30k bonus), the memory access after free (a $30k bonus), incorrect pointer handling (a $30k bonus). In two demos, already known, but not fixed, vulnerabilities were used (two bonuses of 15 thousand dollars). In addition, a sixth attempt to attack Ubuntu was made, but the exploit did not work.
About the components of the problem are not yet reported, according to the terms of the competition, detailed information about all demonstrated zero day vulnerabilities will be published only after 90 days, which are given for the preparation of updates by manufacturers to eliminate vulnerabilities.
About the other demos of successful attacks the following is mentioned:
- Three Oracle VirtualBox hacks exploiting vulnerabilities caused by Memory Access After Free Vulnerabilities, Buffer Overflow, and Read Out of Buffer (two $40k bonuses and $80k bonus for exploiting 3 vulnerabilities that allowed execution of code on the host side).
- Apple's macOS Elevation ($40K Premium).
- Two attacks on Microsoft Windows 11 that allowed them to increase their privileges ($30.000 bonuses).
- The vulnerabilities were caused by post-free memory access and incorrect input validation.
- Attack on Microsoft Teams using a chain of two bugs in the exploit ($75,000 premium).
- Attack on Microsoft SharePoint ($100,000 bonus).
- Attack on VMWare workstation by accessing free memory and an uninitialized variable ($80 premium).
- Code execution while rendering content in Adobe Reader. A complex chain of 6 errors was used to attack, bypass the sandbox, and access the banned API ($50,000 prize).
Two attacks on Tesla car infotainment system and Tesla Gateway, allowing to gain root access. First prize was $100,000 and a Tesla Model 3 car, and second prize was $250,000.
The attacks used the latest stable versions of applications, browsers, and operating systems with all available updates and default settings. The total amount of compensation paid was $1,035,000 and a car. The team with the most points received $530,000 and a Tesla Model 3.
Finally, if you are interested in knowing more about it, you can consult the details In the following link.